πby3 Security Operations: Protecting Your Digital Future
At πby3, we prioritize security at every level. Businesses trust us daily with their most valuable digital assets, and we are committed to safeguarding these with the highest cybersecurity standards.
Our approach is driven by putting clients first and evolving with emerging cyber threats. Through innovative solutions, we ensure that your organization is always protected and secure.
Cloud Security Posture Management (CSPM): Strengthening Your Cloud Ecosystem
At πby3 Security Operations, we understand that modern enterprises require robust security solutions that evolve with the digital landscape. Our comprehensive services include advanced Cloud Security Posture Management (CSPM), empowering organizations to maintain complete visibility and control over their cloud infrastructure.
Our CSPM solutions continuously monitor your cloud environments, detecting misconfigurations, compliance violations, and security gaps in real-time. Through automated security assessments and risk visualization, we help you maintain a strong security posture across multiple cloud platforms while ensuring regulatory compliance.
By partnering with πby3, you gain:
- Unified Cloud Monitoring: Consolidated view of all cloud assets to identify potential risks and optimize configurations.
- Automated Risk Detection: Advanced tools to prioritize and resolve threats efficiently.
- Regulatory Compliance Checks: Continuous monitoring to ensure adherence to global standards like GDPR, HIPAA, and ISO/IEC 27001.
- Proactive Threat Remediation: Addressing vulnerabilities promptly to safeguard sensitive data and maintain operational continuity.
With CSPM as a core component of our security strategy, πby3 ensures your cloud ecosystem remains secure, resilient, and compliant with evolving industry standards.
Our Security Philosophy: Always On, Always Secure
A proactive, multi-layered approach combines cutting-edge technology, industry expertise, and proven practices to minimize risks and ensure business continuity.
- Confidentiality: Protect sensitive data from unauthorized access.
- Integrity: Ensure data accuracy and consistency.
- Availability: Guarantee accessibility when needed.
Comprehensive Security Measures
Our security practices safeguard your infrastructure with comprehensive measures from detection to remediation.
- Threat Detection & Incident Response
- 24/7 Monitoring & Detection: Continuous surveillance of your systems to identify potential risks and respond swiftly.
- Real-time Alerts: Immediate notifications to allow for a quick response.
- Incident Handling & Remediation: Rapid, coordinated response to minimize the impact of breaches, including forensics support to prevent recurrence.
- Vulnerability Management
- Proactive Scanning: Regular identification of vulnerabilities to prevent breaches.
- Patch Management: Keeping all systems updated to avoid known exploits.
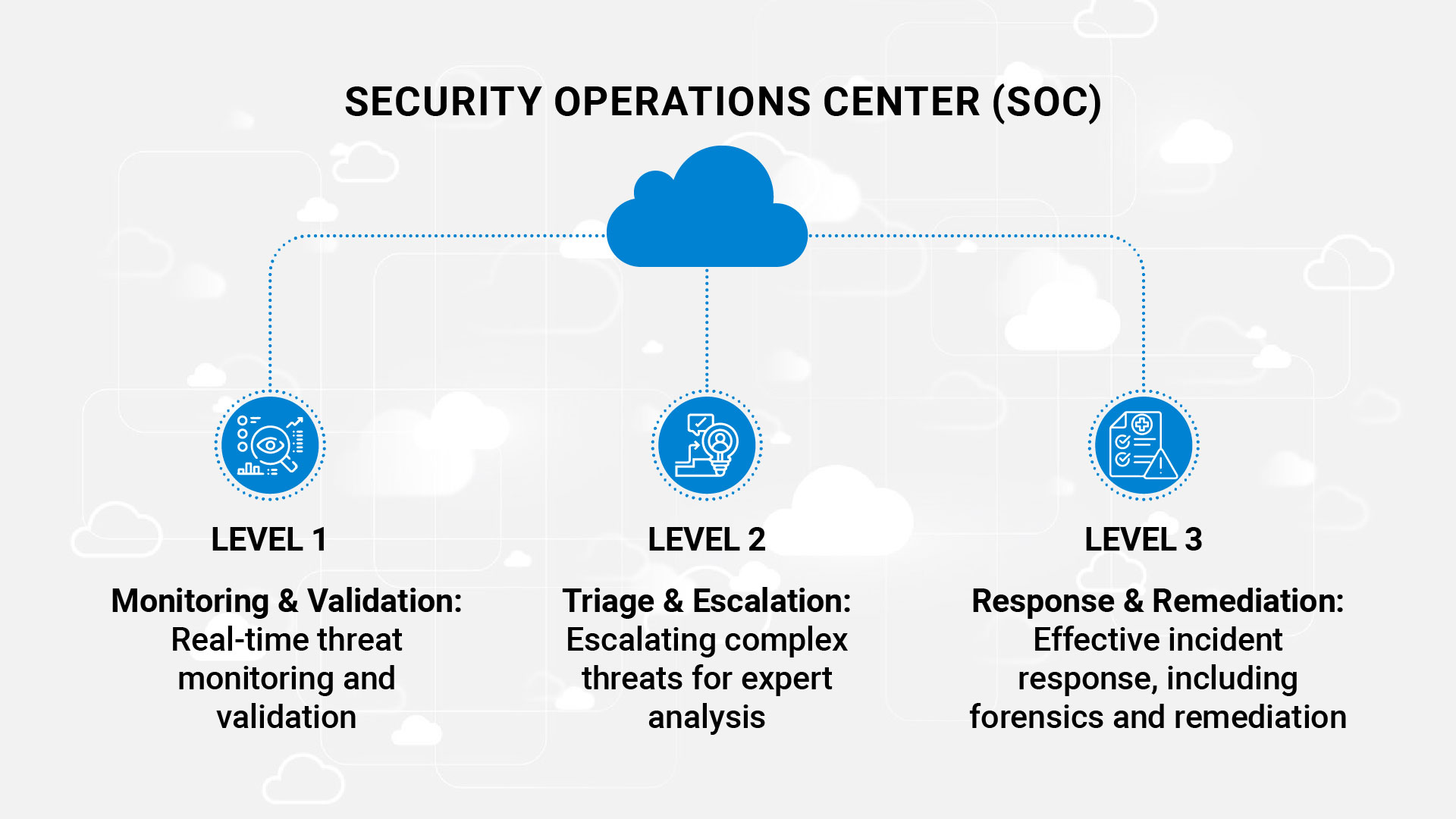
Our SOC ensures around-the-clock protection for your assets by handling threats with precision.
- Level 1 - Monitoring & Validation: Real-time threat monitoring and validation.
- Level 2 - Triage & Escalation: Escalating complex threats for expert analysis.
- Level 3 - Response & Remediation: Effective incident response, including forensics and remediation.
Elevating Security with Reporting & Service Management
We provide clear, actionable insights that improve your security posture, enabling better decisions.
- KPI Reporting: Track performance with actionable security metrics.
- Threat Scorecards: Visualize and monitor security trends.
- Custom Risk Advisories: Personalized risk insights for proactive action.
- Incident Metrics & Dashboards: Analyze incident trends and visualize security data.
Security isn't static; it's a continuous journey of improvement.
- Strategy Development: Craft a robust security strategy alongside our experts.
- Policy Guidance: Align with regulatory standards and best practices.
Continuous Monitoring & Governance
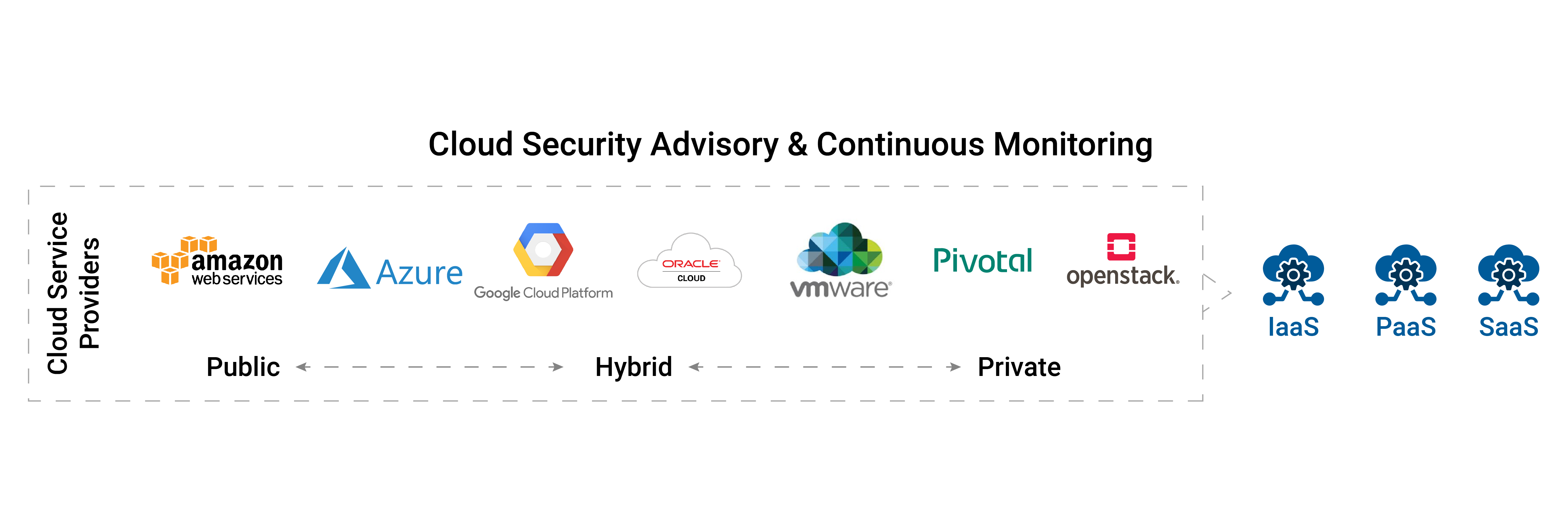
πby3 provides sustained security through constant monitoring and effective risk management.
- 24/7 Surveillance: Proactive monitoring and real-time threat detection.
- Identity & Access Management (IAM): Strict controls over who accesses your systems.
- Compliance Support: Help navigating regulatory requirements for peace of mind.
Data Privacy and Compliance
We are fully committed to securing your data while ensuring privacy and compliance with global standards:
- GDPR & ISO/IEC 27001 Compliance: Adherence to privacy laws and security best practices.
- Industry Standards: Compliance with PCI-DSS, HIPAA, and other relevant frameworks.
Your Security, Our Priority
With πby3, security is an ongoing commitment. Our expert SOC team and advanced technologies ensure your business remains secure against evolving threats.